How phishing can ruin the good name of an online brand
Phishing is a type of cyber-attack where cyber-criminals use email as a disguised weapon for tricking customers.
Phishing attacks steal client data, login credentials, bank account numbers, credit card numbers, etc. The attackers impersonate themselves as a trusted source by sending an email for deceiving the email recipient. They entice them into believing that the email is received from genuine sources, like the victim’s bank, new job opportunities, or other important identities.

Once the email recipient is lured into believing the email, they are asked to click or download a malicious link present in the fake email. This mouse click can lead to a malware installation or ransomware attacks, which can divulge sensitive information.
It’s always unpleasant to dip feet in phishing waters. Just as hooks are needed to catch fish, the same method (hooking via email) is used for grabbing information. Since hackers use sophisticated techniques for phishing attacks, the severity of these attacks are constantly increasing.
Recruiter indicates that Phishing accounts for 90% of all data breaches.
Popular successful phishing scams:
- Hacking of John Podesta’s account (Clinton’s campaign chairman) for his Gmail password
- Hacking into the University of Kansas to steal instructors’ confidential login information
What are phishing kits?
When I mentioned that hackers find their way through computers and networks, I was not exaggerating because when they decide to carry out phishing attacks, phishing kits are a great help. These kits used to serve as back-end processes for launching phishing attacks. So even cyber-criminals with minimal technical experiences could launch successful phishing attacks.
All the resources and tools needed for a phishing website were available in the phishing kit.
The phishing cycle:
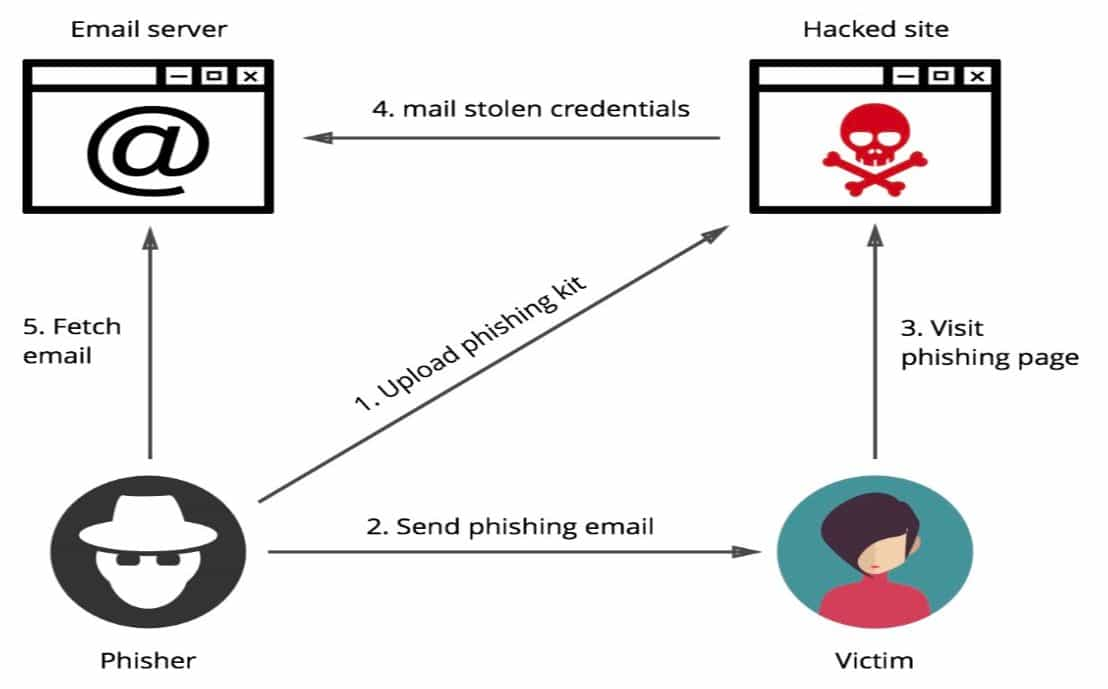
The hacker can install the phishing kit on a website and start sending emails to prospective victims. The design of the kit is such that it looks like a perfect replica of a legitimate site.
Phishing kits and tools are widely available online, especially on the Dark Web.
How do phishing attacks work?
The most successful phishing attacks happen when an unassuming person is targeted, and they willingly enter their information into the phishing page. Since asking for information is the easiest way to gain the needed information, phishing attacks rule the cyber-attack world.
These attacks are personalized to individuals who are unaware that they are attacked, and so these attacks tend to look like typical business conversations.
Consider a top executive in the HR department who is utilizing the recruitment services of XYZ agency. This agency sends him an email about a job posting which he had recommended, and now the agency is asking for some more details needed to add in the link mentioned in the email.
Naturally, you don’t doubt anything here, so you click the link and enter the details willingly. And right there — you are phished!
You may not realize you have been phished until the damage is already done. Even if you recycle passwords frequently, these attackers can create hundreds of social media accounts to dupe you by emerging as a legitimate source.
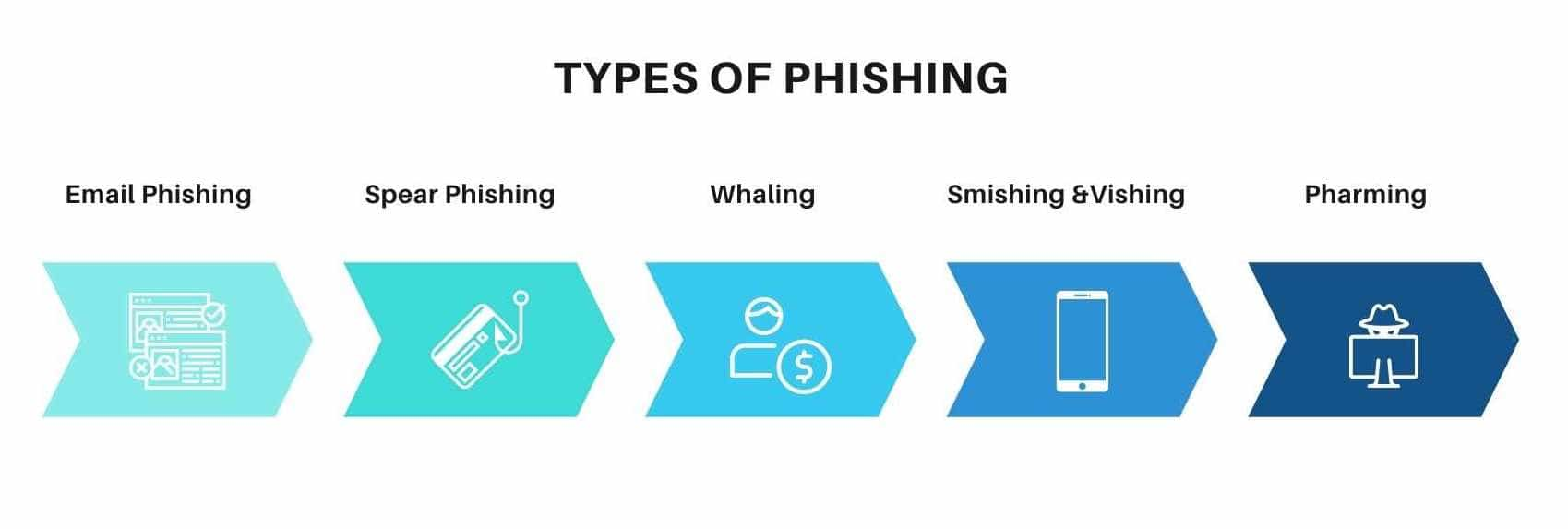
Types of phishing
All these crooks have the same goal, but they have multiple ways to achieve it. Let’s have a look at some of the most popular types of phishing attacks.
Email phishing
The majority of phishing attacks are made by sending emails. A fake domain, which is a mirror of the genuine one, is created by fraudsters and sent to thousands of people at a time. They may request things like:
- Login credentials
- Passwords
- Bank account numbers
Since they impersonate familiar individuals or organizations, users instantly turn into victims.
These fake domains usually have a minor difference in spelling, like the letters “r” and “n” can be used together as “rn” to look like an “m.”
The best way to spot phishing emails is to stay alert and keep a look out for warning signals by re-checking the email address before clicking on these links or downloading attachments.
Spear phishing
Spear phishing is an attack made to a specific person or a specific organization via email. Fraudsters keep track of the victim and have all of their personal details like:
- Address
- Phone number
- Hometown
- Friends
- Email address
- Job designation
And many more.
Research by Proofpoint indicates that nearly 90% of companies have faced spear phishing attacks.
Whaling
Whaling attacks are targeted at senior executives (CEOs, MDs, CTOs, or any other individuals having top-notch designations). These high-profile individuals tend to use personal email ids for business interactions, which may lack corporate web protections.
Though whaling attacks tend to take time, they promise high payoffs. Since attackers use actual corporate logos and spoofed email addresses for making communication look genuine, and show that they are from trustworthy sources, duping becomes simpler.
For example, one of the most notable corporate cyber-crimes involved an employee of The Scoular Co. who was duped of $17.2 million by whaling.
Smishing & vishing
In both these phishing attacks, emails are replaced by mobile phones for communicating with victims. Here the user is lured into downloading a virus or trojan horse into their mobile device. Vishing is carried out by using voice technology.
Pharming
Pharming is done by injecting malicious codes into the system. It redirects system traffic to fake sites created by hackers. This can be done without the victim’s awareness.
How to prevent phishing attacks
Appropriate measures by individuals as well as companies need to be taken for preventing these attacks. Here’s a quick checklist of things to do to prevent phishing attacks:
- Educate your employees regularly by conducting training sessions and keep them aware of the latest crime trends.
- Always double-check the spellings in the URL as well as in the links attached.
- Checkout URL redirects for identical web patterns.
- Contact the firm or individual directly in case of suspicions.
- Beware of posting personal information on social media.
- Enable 2FA (2-factor authentication) for preventing these attacks.
- Implement strict password policies.
- Prevent employees from clicking on external or unknown email links. A better option is to type the URL in the browser and visit the site.
- Buy an SSL certificate and install the same on the website. There are cheap SSL certificates that provide robust encryption securities and store information in an encrypted format.
- Deploy email filters that allow you to prevent email spoofing by removing spam emails and phishing emails.
- Implement DKIM (Domain Keys Identified Mail), Domain-Based Message Authentication, or Reporting and Conformance (DMARC), which secure your domain against email spoofing attacks.
- Keep your web securities updated with the latest security patches.
- Install anti-virus solutions and update them regularly.
- Never give away your personal information without checking the legitimacy of the website. Always ensure “HTTPS” before submitting any data.
- Ignore hoax calls wherein your sensitive information is collected for giving other benefits.
- Never progress on sites containing suspicious or malicious content. Delete these sites immediately to prevent further damages.
- Never download files with caution warning: “This file can harm your device.”
Apart from the above precautions, there are a few tips for the IT department too:
- Keep a check on user click links.
- Inspect web traffic.
- Take a mock test of employees for spotting phishing emails or loopholes in web security.
Final thoughts
Though hackers tend to make smart moves to achieve their goals, pertinent steps taken by a company or an individual can eliminate these threats. Trained employees can help prevent these attacks, since they know the signs, the risks, and the steps to address them.
Educated employees and congruous web security strategies can protect your company against malicious phishing attacks.
Tags: Personal Branding.